5 Things to be Aware of When Buying WordPress Security
This is an excellent article written by Mark Maunder, Chief Executive Officer at Wordfence and was published on the Wordfence Blog on December 14, 2016. While they are selling a service, there is good insight into how WordPress security services stack up.
Update: Umbrella Host reached out to us about an article that compliments “5 Things to be Aware of When Buying WordPress Security” nicely, addressing “How to Clean a Hacked WordPress Website“.
+++++
If you are new to WordPress or reevaluating your security strategy, you are overwhelmed by choice in today’s market. The reality is that there are only a handful of tools that truly protect your WordPress website from a hack and help you detect an incident. With all of the claims that vendors are making, it can be tough to choose the most effective product to protect your investment and your customer data.
To help you in your decision making, I’m going to call out 5 things in this post that you need to be aware of before you choose a security plugin, a cloud solution or something that runs in the hosting environment that your hosting provider is selling.
1. Not all security products include a firewall
Many of the best known security plugins for WordPress don’t actually include a firewall. To understand this, it’s important to understand what a firewall actually is. The firewall in Wordfence is known as a Web Application Firewall or ‘WAF’.
For a WAF to be effective, it needs to fulfill a few basic requirements:
- It needs to block a wide range of attacks based on it’s ability to recognize website requests as attacks. Types of attacks include SQL injection attacks, remote code execution, cross site scripting and cross site request forgery attacks.
- The WAF needs to have a rule-set that is continuously updated. These rules are used to recognize attacks and block them. They can’t be updated only when the software is upgraded. They need to be updated constantly via a ‘feed’.
- The WAF needs to analyze ALL requests, not just requests that hit a particular application. In other words, if you have installed a WordPress WAF, it must block requests that try to directly access a script in a WordPress subdirectory along with requests that hit WordPress itself.
- The WAF needs to be very high performance. It will be inspecting every request that hits your site and it’s very important it doesn’t slow your site down at all.
Wordfence fulfills all these requirements. It has a comprehensive rule-set that blocks a wide range of attacks and is continuously updated via our Threat Defense Feed. The Wordfence WAF inspects every request made to a PHP application on your website. Whether it’s a WordPress request or a direct attack on a script like Timthumb, Wordfence will see it and analyze it and block it if necessary. Wordfence is extremely high performance. Wordfence uses use core PHP functionality for our rule-set that executes very fast, pre-filtering rules and only execute what is relevant and our rule-set is highly optimized.
Many popular security plugins for WordPress don’t include a WAF, or firewall. They include features like brute-force protection, file change detection, backups, strong password enforcement and so called system ‘tweaks’. But they don’t include the most basic security component of them all: An effective web application firewall.
When purchasing a security product, make sure it actually includes a firewall.
2. Cloud firewalls can be bypassed and don’t have identity data
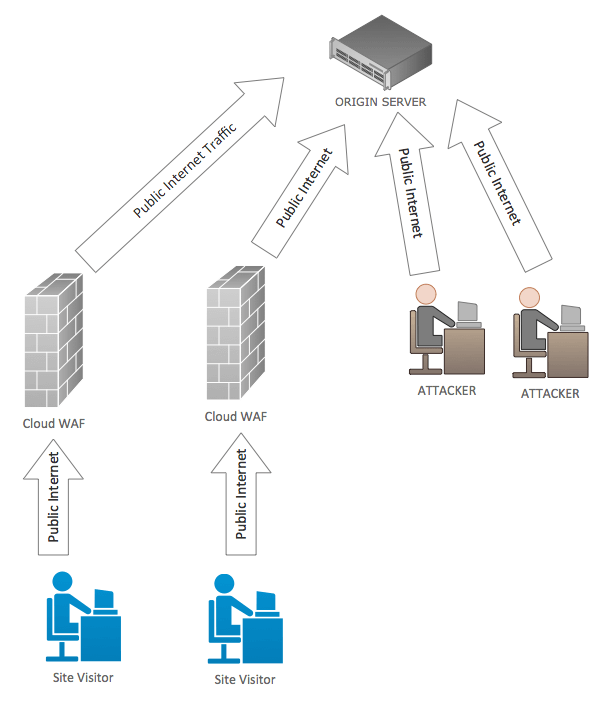 Because cloud firewalls execute on remote servers out on the Internet, it’s possible for an attacker to go around them and attack your site directly. Wordfence has written about this in some detail.
Because cloud firewalls execute on remote servers out on the Internet, it’s possible for an attacker to go around them and attack your site directly. Wordfence has written about this in some detail.
Because cloud firewalls execute remotely, they don’t have access to your WordPress API and database. That means they don’t know basic things like: “Is a user signed into your website or not?” They don’t have this data so they can’t use it in their decision making about who to allow and who to block.
If you don’t even know whether a request is coming from a site administrator or an attacker, how can you provide effective protection? Wordfence has written about the cloud WAF user identity problem in some detail.
Cloud firewalls also use a rule-set that is generic. Their rules are designed for all websites. That means they don’t specialize in a specific platform. The result is that they can allow through some of the best known and most basic attacks on a platform like WordPress.
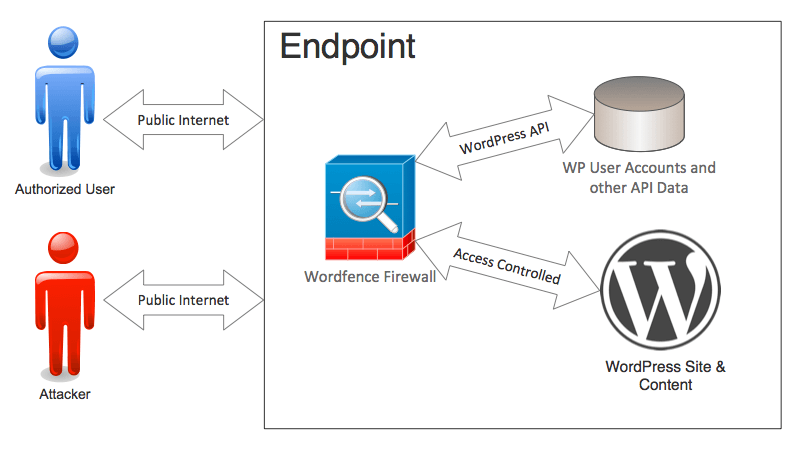 Wordfence is designed specifically for WordPress, it knows and uses user identity to make it’s decisions and it’s not possible to go around the Wordfence web application firewall because it runs directly on your WordPress website.
Wordfence is designed specifically for WordPress, it knows and uses user identity to make it’s decisions and it’s not possible to go around the Wordfence web application firewall because it runs directly on your WordPress website.
3. Some malware scans don’t check very much
When choosing a malware scanner for WordPress, it’s important to choose one that does a deep thorough scan of your site. Malware authors have become very creative in how and where they hide malware once they’ve compromised your website. Without a deep scan, your site may be infected and you won’t be aware of it.
iThemes Security, the second most popular security plugin for WordPress, uses Sucuri Sitecheck to perform a malware scan. You have to pay for iThemes Pro to gain access to this feature, which currently costs $48 per year.
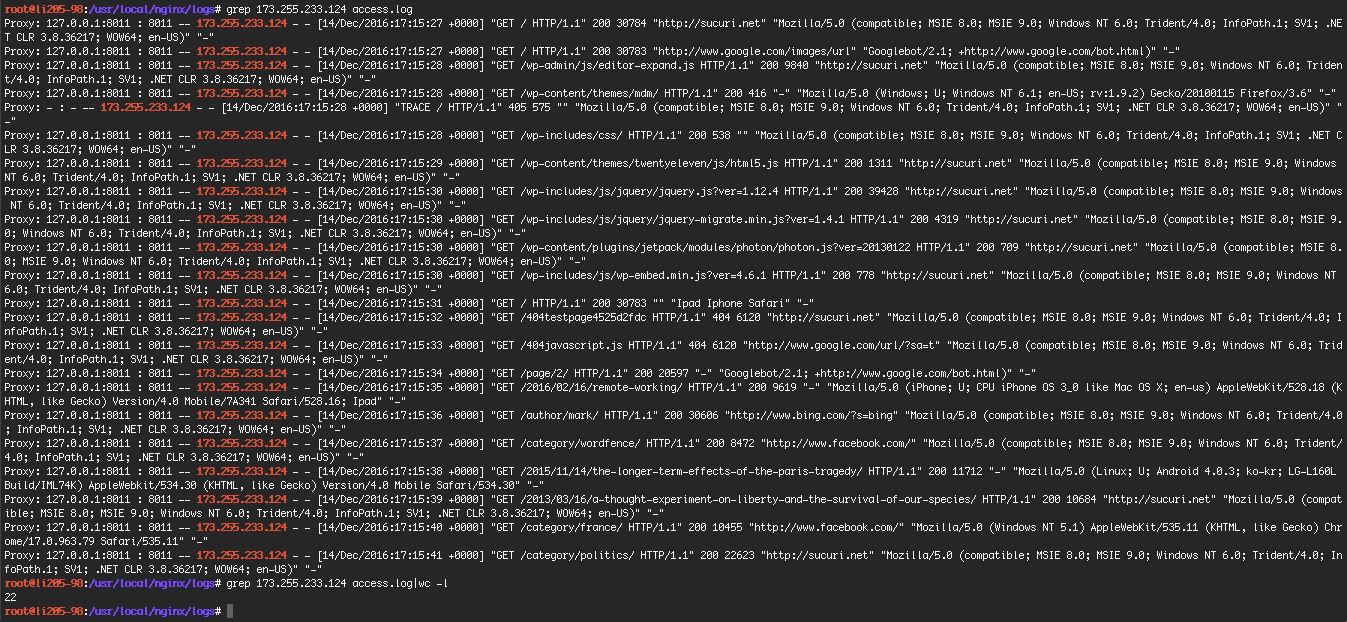
Once you’ve paid for iThemes security and have access to the malware scan feature, you can launch a scan. A Sucuri scan using iThemes Security on my test WordPress site only performed 22 page requests. All the checks are remote, so no source code is inspected.
After doing this scan, this is what my logfile looks like.
As you can see, it didn’t do very much.
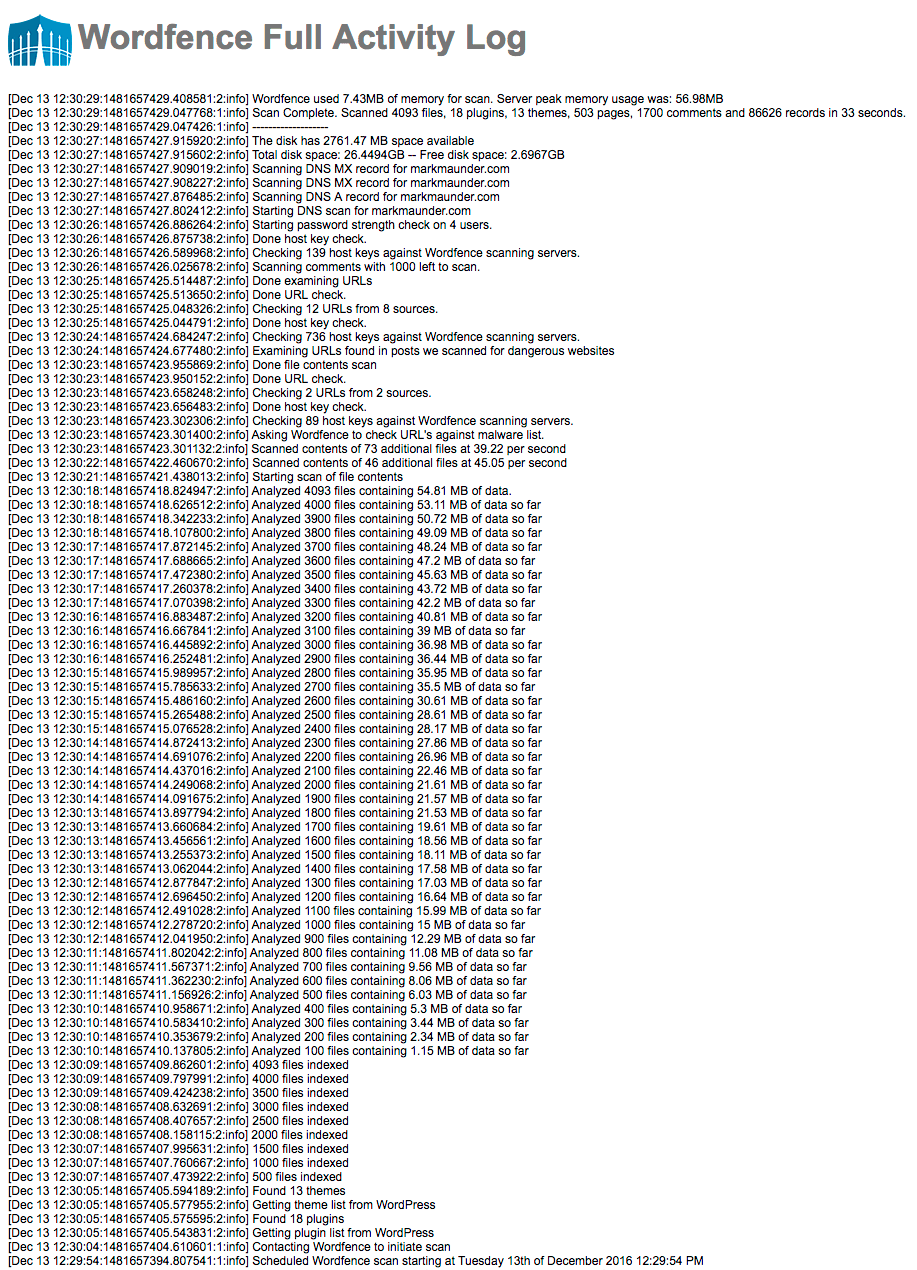
Below looking at what a typical free Wordfence scan looks like (it’s in reverse chronological order). As you can see Wordfence analyzes the source code of over 4,000 files on the same site and perform a host of other checks.
When choosing a malware scanner, make sure you pick one that performs a comprehensive scan of your website and doesn’t just do a cursory check. Malware can be hard to find and well hidden. Wordfence performs a deep and comprehensive scan of your site every time it runs.
4. Malware scanning takes a team, forensic work and processes
 Have you wondered why our Wordfence site cleaning service is is so reasonably priced, even though you get your own Wordfence analyst working closely with you to fix your hacked site?
Have you wondered why our Wordfence site cleaning service is is so reasonably priced, even though you get your own Wordfence analyst working closely with you to fix your hacked site?
It’s because your hacked website is an amazing source of forensic data for us. Wordfence takes the footprints that a hacker left behind and add that to our malware scan.
To provide an effective malware scan, you need to perform hands-on forensic analysis of the latest attacks as they happen. That’s what our site cleaning team does.
Then you need to take that attack data and run it through a process to turn it into threat intelligence and distribute it, in real-time to a great malware scanner. That is what our Threat Defense Feed is. The TDF describes our process of gathering, analyzing and distributing threat intelligence to the Wordfence malware scanner and firewall.
I’m not currently aware of a single WordPress specific malware scanner that combines a high performance scan engine with a team and process like Wordfence does.
5. Watch out for “automated” malware removal
Some companies offer an “automated” fix if they detect malware on your website. When Wordfence first heard about this, it viewed the concept with deep skepticism. If malware is detected on a website, it has been compromised. The definition of a ‘compromised’ site is that someone unauthorized has gained access to the site.
Incident response is a complex field. Wordfence has certified forensic investigators on our team who have developed our site cleaning process. To get an idea of how the a typical incident response process works, you can reference NIST publication 800-61 “Computer Security Incident Handling Guide” [PDF].
In general, forensic analysts will divide incident handling into three phases:
- Detection and Analysis: This includes analyzing attack vectors, documenting the incident, prioritization and notification.
- Containment, eradication and recovery: This includes evidence gathering, identifying what has been attacked and evidence gathering.
- Post incident activities: In this phase forensic data is analyzed, evidence is retained and the data is used to prevent future incidents.
There are several different approaches to incident response and you can visit OWASP to learn more about how they tackle the problem.
If a site is compromised, an automated fix would leave out many of these steps. For example, it would not be able to determine how an attacker gained access and so the site may be repeatedly hacked.
We recommend that you avoid products that claim an automated fix is possible for a compromised website. Instead, use a security analyst trained in incident response to help fix your hacked website.